-
Add-ons
- Access Control Testing
-
Active Scan Rules
-
Active Scan Rules - Alpha
-
Active Scan Rules - Beta
-
Advanced SQLInjection Add-on
- AJAX Spider
- Alert Filters
- All In One Notes
-
AMF Support
-
Authentication Helper
- Authentication Report - JSON
- Authentication Request Identification
- Authentication Tester Dialog
- Auto-Detect Authentication
- Auto-Detect Session Management
- Browser Based Authentication
- Client Script Authentication
- Report Templates
- Header Based Session Management
- Session Management Identification
- Verification Request Identification
-
Authentication Statistics
-
Automation Framework
- Automation Framework - About
- Automation Framework - authentication
- Automation Framework - Environment
- Automation Framework - GUI
- Automation Framework - addOns Job
- Automation Framework - activeScan Job
- Automation Framework - activeScan-config Job
- Automation Framework - activeScan-policy Job
- Automation Framework - delay Job
- Automation Framework - exitStatus Job
- Automation Framework - passiveScan-config Job
- Automation Framework - passiveScan-wait Job
- Automation Framework - requestor Job
- Automation Framework - spider Job
- Automation Framework - Options
- Automation Framework - Alert Job Test
- Automation Framework - Monitor Job Test
- Automation Framework - Statistics Job Test
- Automation Framework - URL Presence Job Tests
- Automation Framework - Job Tests
-
Bean Shell Console
-
BIRT Reports
-
Browser View
-
Bug Tracker
-
Call Graph
-
Call Home
-
Client Side Integration
- Client Side Integration - AJAX Spider Enhancement
- Client Side Integration - Automation Framework Support
- Client Side Integration - Firefox Profile
- Client Side Integration - Internals
- Client Side Integration - Passive Scan Rules
- Client Side Integration
- Client Side Integration - Client Spider API
- Client Side Integration - Client Spider
-
Code Dx
-
Collection: Pentester Pack
-
Collection: Scan Rules Pack
- Common Library
-
Community Scripts
- Custom Payloads
-
Custom Report
-
Database Add-on
-
Dev Add-On
-
Diff
-
Directory List v1.0
-
Directory List v2.3
-
Directory List v2.3 LC
- DOM XSS Active Scan Rule
- Encode / Decode / Hash dialog
-
Eval Villain
-
Export Report
- Forced Browse
-
Form Handler
-
Foxhound
- Fuzz AI Files
-
FuzzDB Files
-
FuzzDB Offensive
-
FuzzDB Web Backdoors
- Fuzzing
-
Getting Started Guide
-
GraalVM JavaScript
- GraphQL Support
- Groovy Support
- gRPC Support
-
Highlighter
-
HTTPS Info
- The HUD
- Import/Export
-
Import URLs
- Insights Add-on
- Invoke Applications
-
JSON View
-
Kotlin Support
-
Linux WebDrivers
-
Log File Importer
-
macOS WebDrivers
-
Neonmarker
- Network Add-on
- Out-of-band Application Security Testing Support
-
Online Menu
- OpenAPI Support
- Parameter Digger
-
Passive Scan Rules
-
Passive Scan Rules - Alpha
-
Passive Scan Rules - Beta
- Passive Scanner Add-on
- Plug-n-Hack
- Port Scan
- Postman Support
- Python Scripting
- Quick Start
-
Regular Expression Tester
- Replacer
-
Report Alert Generator
-
Report Generation
- Report Generation - About
- Report Generation API
- Report Generation Automation Framework Support
- Creating Reports
- High Level Report Sample
- Modern HTML Report with themes and options
- Risk and Confidence HTML
- SARIF JSON Report
- Traditional HTML with Requests and Responses
- Traditional HTML
- Traditional JSON Report with Requests and Responses
- Traditional JSON Report
- Traditional Markdown Report
- Traditional PDF
- Traditional XML Report with Requests and Responses
- Traditional XML Report
- Report Templates
- Requester Add-on
- Retest
-
Retire.js
-
Reveal
-
Revisit
-
Ruby Scripting
-
SAML Support
-
Save Raw Message
-
Save XML Message
- Scan Policies
- Script Console
- Selenium
- Sequence Scanner
- Server-Sent Events
- SOAP Support
-
Software Risk Manager
- Spider
-
SVN Digger Files
- Technology Detection
-
Tips and Tricks
-
TLS Debug
- Token Generation and Analysis
-
TreeTools
-
Value Generator
-
ViewState
- WebSockets
-
Windows WebDrivers
-
Zest
-
Releases
- Release 1.0.0
- Release 1.1.0
- Release 1.2.0
- Release 1.3.0
- Release 1.3.1
- Release 1.3.2
- Release 1.3.3
- Release 1.3.4
- Release 1.4.0
- Release 1.4.1
- Release 2.0.0
- Release 2.1.0
- Release 2.10.0
- Release 2.11.0
- Release 2.11.1
- Release 2.12.0
- Release 2.13.0
- Release 2.14.0
- Release 2.15.0
- Release 2.16.0
- Release 2.16.1
- Release 2.17.0
- Release 2.2.0
- Release 2.2.1
- Release 2.2.2
- Release 2.3.0
- Release 2.3.1
- Release 2.4.0
- Release 2.4.1
- Release 2.4.2
- Release 2.4.3
- Release 2.5.0
- Release 2.6.0
- Release 2.7.0
- Release 2.8.0
- Release 2.9.0
-
Getting Started
- Scanner Rules
-
Features
- Add-ons
- Alerts
- Anti CSRF Handling
- API
- Active Scan
- Authentication
- Authentication Methods
- Authentication Verification Strategies
- Breakpoints
- Callbacks
- Contexts
- Custom Page
- Data Driven Content
- Globally Excluded URLs
- HTTP Sessions
- Manipulator-in-the-middle Proxy
- Marketplace
- Modes
- Notes
- Passive Scan
- Software Bill of Materials
- Scan Policy
- Scope
- Scripts
- Session Management
- Sites Tree
- Spider
- Statistics
- Structural Modifiers
- Structural Parameters
- Tags
- Users
- A Basic Penetration Test
- Configuring Proxies
-
Desktop UI Overview
-
Dialogs
- Add Alert dialog
- Add/Edit Breakpoint dialog
- Add Note dialog
- Active Scan dialog
- Encode / Decode / Hash dialog
- Find dialog
- History Filter dialog
- Manual Request Editor dialog
- Manage Add-ons
- Manage History Tags dialog
-
Options dialog
- Options Alerts screen
- Options Anti CRSF screen
- Options API screen
- Options Active Scan screen
- Options Active Scan Input Vectors screen
- Options Breakpoints screen
- Options Callback Address screen
- Options Client Certificate screen
- Options Check for Updates screen
- Options Connection screen
- Options Database screen
- Dynamic SSL Certificates
- Options Extensions screen
- Options Global Exclude URL screen
- Options HTTP Sessions screen
- Options JVM screen
- Options Keyboard screen
- Options language screen
- Options Local Proxies screen
- Options Passive Scan Tags screen
- Options Passive Scanner Screen
- Options Passive Scan Rules Screen
- Options Rule Configuration screen
- Options Scripts screen
- Options Search screen
- Options Spider screen
- Options Statistics screen
- Options Display screen
- Persist Session dialog
- Scan Policy Dialog
- Scan Policy Manager dialog
- Scan Progress Dialog
- Session Properties dialog
- Spider dialog
- Footer
- The Tabs
- Top Level Menu
- Top Level Toolbar
- Views
-
Dialogs
gRPC Support
This add-on will allow you to inspect, attack gRPC endpoints, decode and encode protobuf messages.
The add-on is still in an early stage, so the range of its functionality is limited. However, you can combine it with existing ZAP functionality to abuse gRPC endpoints in many different ways.
Introducing the gRPC Add-on
This add-on aims to simplify the testing process by providing tools for:
- Encoding and Decoding: Easily encode and decode Protobuf messages for testing purposes.
- Testing gRPC Endpoints: You can combine it with existing ZAP functionality to abuse gRPC endpoints in many different ways.
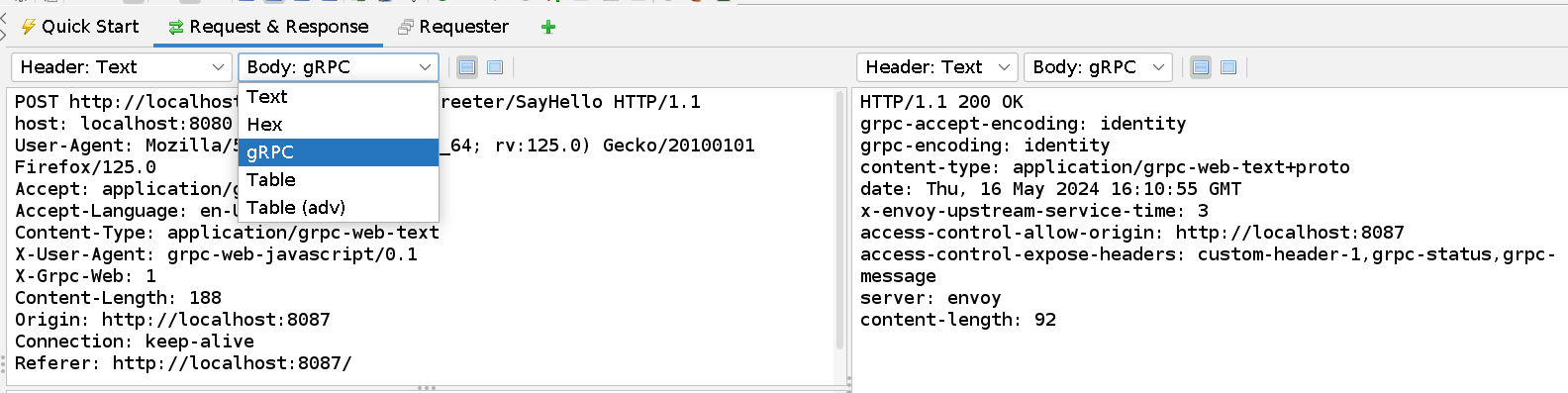
How to see gRPC decoded Message
In the Message View panel, change the Body to gRPC.
Understanding Decoded Protobuf Messages
When decoding Protobuf messages, it’s essential to understand the structure of the decoded data. Protobuf messages consist of fields, each with a field number, wire type, and value. Let’s delve deeper into these components:
Field Structure
- Field Number: Each field in a Protobuf message is assigned a unique field number. This number is used to identify and distinguish between different fields within the message.
- Wire Type: The wire type determines how the field’s value is encoded and provides information about the type of data stored in the field.
- Value: The actual data contained within the field, encoded according to its wire type.
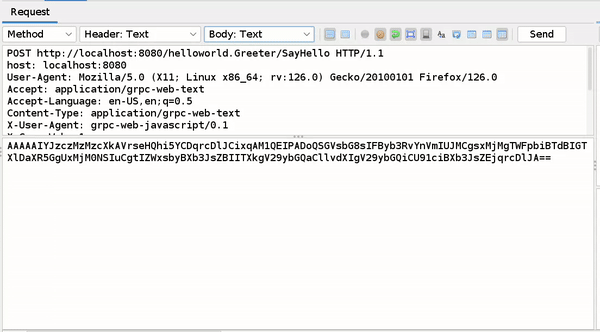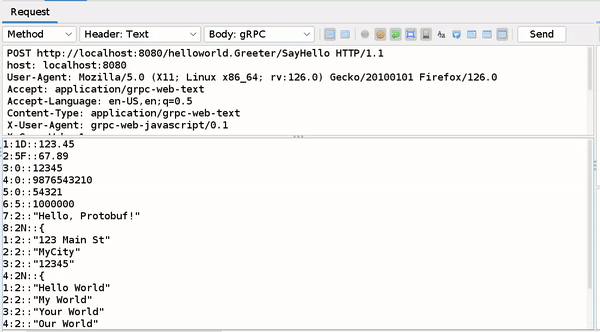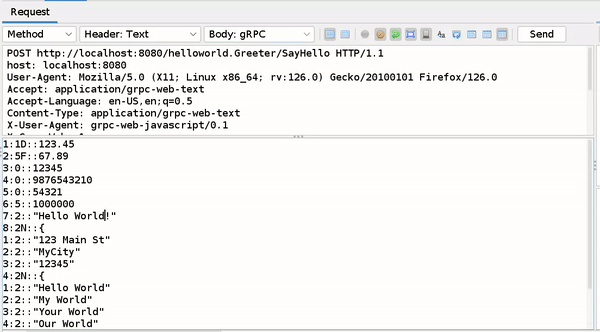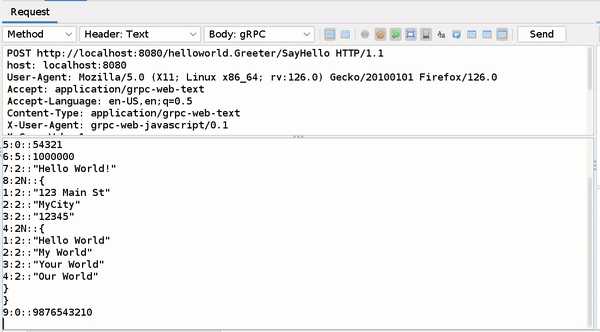
Let’s understand the decoded Protobuf Message Structure using below example
This is the Base64 encoded form of the binary text received by ZAP.
AAAAAIYJZCZMzMzcXkAVrseHQhi5YCDqrcDlJCixqAM1QEIPADOQSGVsbG8sIFByb3RvYnVmIUJMCgsxMjMgTWFpbiBTdBIGT X1DaXR5GgUxMjMONSIuCgtIZWxsbyBXb3JsZBIITXkgV29ybGQaCllvdXIgV29ybGQiCU91ciBXb3JsZEjqrcDLJA==
On the left side, we have the original message retrieved by the gRPC endpoint in the backend. On the right side, we have the decoded message from the above encoded text, processed by the ZAP gRPC addon.
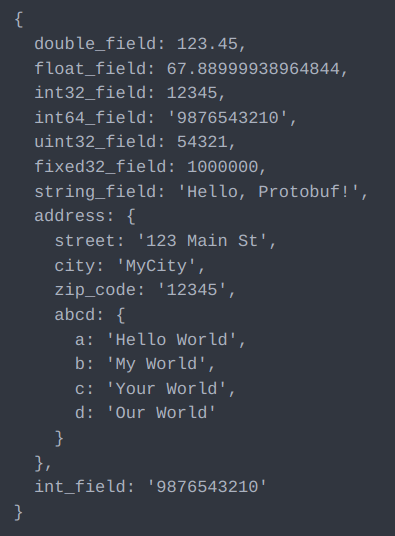
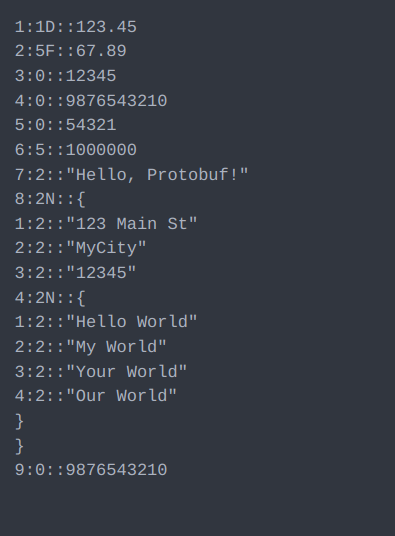
- Each field in the message is represented as “field number:wire type::value”.
- Each key-value pair starts on a new line.
- Additional specifiers are only used for double (
1D), float (5F), and nested messages (2N). - For wire type
2, the value should be enclosed in double quotes, except for nested messages (2N). - For nested messages(
2N):- After the field number and wire type (
fieldNumber:2N::), an open curly brace is placed and start adding nested message fields from new line. - The nested message is closed with a closing curly brace on a separate new line.
- After the field number and wire type (
- Please don’t use unnecessary space.
Writing and Editing Decoded Protobuf Messages
You can only edit this Decoded Message in Requester and Manual request editor window simply change the part after ("::") which contain value or you can write new fields by following above mentioned rules.
See also
| gRPC Variant | for information about the gRPC variant. | |
| gRPC WebSocket | for information about the gRPC WebSocket Support. |